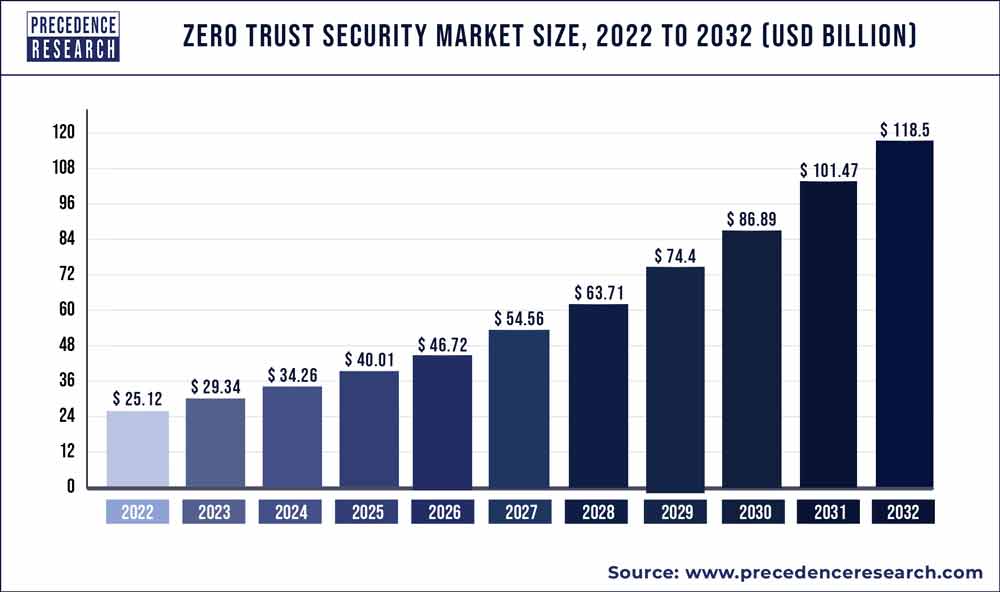
The zero trust security market size is poised to grow by USD 118.5 billion by 2032 from USD 25.12 billion in 2022, exhibiting a CAGR of 16.78% during the forecast period 2023-2032.
Precedence Research has conducted a comprehensive market study that provides valuable insights into the performance of the market during the forecast period. The study identifies significant trends that are shaping the growth of the Zero trust security market. In this recently published report, essential dynamics such as drivers, restraints, and opportunities are highlighted for both established market players and emerging participants involved in production and supply.
To begin with, the Zero trust security Market report features an executive summary that offers a concise overview of the marketplace. It outlines the key players and industry categories expected to have an impact on the market in the coming years. The executive summary provides an unbiased summary of the market.
Get a Sample Report: https://www.precedenceresearch.com/sample/3170
Zero Trust Security Market Report Scope
| Report Coverage | Details |
| Market Size in 2023 | USD 29.34 Billion |
| Market Size by 2032 | USD 118.5 Billion |
| Growth Rate from 2023 to 2032 | CAGR of 16.78% |
| Largest Market | North America |
| Base Year | 2022 |
| Forecast Period | 2023 To 2032 |
| Segments Covered | By Authentication Types, By Solution Type, and By Deployment Type |
| Regions Covered | North America, Europe, Asia-Pacific, Latin America, and Middle East & Africa |
Read More: Cardiovascular Digital Solutions Market To Rake USD 183.23 Bn By 2032
The empirical study on the global Zero trust security market primarily focuses on the drivers in subsequent sections. It demonstrates how changing demographics are projected to influence the supply and demand dynamics in the Zero trust security Market. Our market report for the Zero trust security market also delves into the significant rules and regulations that are likely to impact the future growth of this sector. Moreover, in order to comprehend the underlying demand factors, industry experts have provided insights into its fundamental origins.
Top Key Players:
- Cisco Systems, Inc.
- Palo Alto Networks, Inc.
- Microsoft Corporation
- Symantec Corporation (now part of Broadcom Inc.)
- Okta, Inc.
- IBM Corporation
- Check Point Software Technologies Ltd.
- Akamai Technologies, Inc.
- Fortinet, Inc.
- CyberArk Software Ltd.
Data Sources and Methodology
To gather comprehensive insights on the Global Zero trust security Market, we relied on a range of data sources and followed a well-defined methodology. Our approach involved interactions with industry experts and key stakeholders across the market’s value chain, including management organizations, processing organizations, and analytics service providers.
We followed a rigorous data analysis process to ensure the quality and credibility of our research. The gathered information was carefully evaluated, and relevant quantitative data was subjected to statistical analysis. By employing robust analytical techniques, we were able to derive meaningful insights and present a comprehensive overview of the Global Zero trust security Market.
The most resonating, simple, genuine, and important causes because of which you must decide to buy the Zero trust security market report exclusively from precedence research
- The research report has been meticulously crafted to provide comprehensive knowledge on essential marketing strategies and a holistic understanding of crucial marketing plans spanning the forecasted period from 2023 to 2032.
Key Features of the Report:
- Comprehensive Coverage: The report extensively encompasses a detailed explanation of highly effective analytical marketing methods applicable to companies across all industry sectors.
- Decision-Making Enhancement: It outlines a concise overview of the decision-making process while highlighting key techniques to enhance it, ensuring favorable business outcomes in the future.
- Articulated R&D Approach: The report presents a well-defined approach to conducting research and development (R&D) activities, enabling accurate data acquisition on current and future marketing conditions.
Zero Trust Security Market Segmentation:
By Authentication Types
- Single-factor Authentication
- Multi-factor Authentication
By Solution Type
- Network Security
- Data Security
- Endpoint Security
- API Security
- Cloud Security
- Others
By Deployment Type
- Cloud
- On-Premises
By Geography
- North America
- Europe
- Asia-Pacific
- Latin America
- Middle East and Africa
Reasons to Consider Purchasing the Report:
- Enhance your market research capabilities by accessing this comprehensive and precise report on the global Zero trust security market.
- Gain a thorough understanding of the overall market landscape and be prepared to overcome challenges while ensuring robust growth.
- Benefit from in-depth research and analysis of the latest trends shaping the global Zero trust security market.
- Obtain detailed insights into evolving market trends, current and future technologies, and strategic approaches employed by key players in the global Zero trust security market.
- Receive valuable recommendations and guidance for both new entrants and established players seeking further market expansion.
- Discover not only the cutting-edge technological advancements in the global Zero trust security market but also the strategic plans of industry leaders.
Table of Content
Chapter 1. Introduction
1.1. Research Objective
1.2. Scope of the Study
1.3. Definition
Chapter 2. Research Methodology (Premium Insights)
2.1. Research Approach
2.2. Data Sources
2.3. Assumptions & Limitations
Chapter 3. Executive Summary
3.1. Market Snapshot
Chapter 4. Market Variables and Scope
4.1. Introduction
4.2. Market Classification and Scope
4.3. Industry Value Chain Analysis
4.3.1. Raw Material Procurement Analysis
4.3.2. Sales and Distribution Channel Analysis
4.3.3. Downstream Buyer Analysis
Chapter 5. COVID 19 Impact on Zero Trust Security Market
5.1. COVID-19 Landscape: Zero Trust Security Industry Impact
5.2. COVID 19 – Impact Assessment for the Industry
5.3. COVID 19 Impact: Global Major Government Policy
5.4. Market Trends and Opportunities in the COVID-19 Landscape
Chapter 6. Market Dynamics Analysis and Trends
6.1. Market Dynamics
6.1.1. Market Drivers
6.1.2. Market Restraints
6.1.3. Market Opportunities
6.2. Porter’s Five Forces Analysis
6.2.1. Bargaining power of suppliers
6.2.2. Bargaining power of buyers
6.2.3. Threat of substitute
6.2.4. Threat of new entrants
6.2.5. Degree of competition
Chapter 7. Competitive Landscape
7.1.1. Company Market Share/Positioning Analysis
7.1.2. Key Strategies Adopted by Players
7.1.3. Vendor Landscape
7.1.3.1. List of Suppliers
7.1.3.2. List of Buyers
Chapter 8. Global Zero Trust Security Market, By Authentication Types
8.1. Zero Trust Security Market, by Authentication Types, 2023-2032
8.1.1 Single-factor Authentication
8.1.1.1. Market Revenue and Forecast (2020-2032)
8.1.2. Multi-factor Authentication
8.1.2.1. Market Revenue and Forecast (2020-2032)
Chapter 9. Global Zero Trust Security Market, By Solution Type
9.1. Zero Trust Security Market, by Solution Type, 2023-2032
9.1.1. Network Security
9.1.1.1. Market Revenue and Forecast (2020-2032)
9.1.2. Data Security
9.1.2.1. Market Revenue and Forecast (2020-2032)
9.1.3. Endpoint Security
9.1.3.1. Market Revenue and Forecast (2020-2032)
9.1.4. API Security
9.1.4.1. Market Revenue and Forecast (2020-2032)
9.1.5. Cloud Security
9.1.5.1. Market Revenue and Forecast (2020-2032)
9.1.6. Others
9.1.6.1. Market Revenue and Forecast (2020-2032)
Chapter 10. Global Zero Trust Security Market, By Deployment Type
10.1. Zero Trust Security Market, by Deployment Type, 2023-2032
10.1.1. Cloud
10.1.1.1. Market Revenue and Forecast (2020-2032)
10.1.2. On-Premises
10.1.2.1. Market Revenue and Forecast (2020-2032)
Chapter 11. Global Zero Trust Security Market, Regional Estimates and Trend Forecast
11.1. North America
11.1.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.1.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.1.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.1.4. U.S.
11.1.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.1.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.1.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.1.5. Rest of North America
11.1.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.1.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.1.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.2. Europe
11.2.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.2.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.2.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.2.4. UK
11.2.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.2.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.2.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.2.5. Germany
11.2.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.2.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.2.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.2.6. France
11.2.6.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.2.6.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.2.6.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.2.7. Rest of Europe
11.2.7.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.2.7.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.2.7.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.3. APAC
11.3.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.3.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.3.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.3.4. India
11.3.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.3.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.3.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.3.5. China
11.3.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.3.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.3.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.3.6. Japan
11.3.6.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.3.6.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.3.6.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.3.7. Rest of APAC
11.3.7.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.3.7.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.3.7.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.4. MEA
11.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.4.4. GCC
11.4.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.4.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.4.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.4.5. North Africa
11.4.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.4.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.4.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.4.6. South Africa
11.4.6.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.4.6.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.4.6.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.4.7. Rest of MEA
11.4.7.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.4.7.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.4.7.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.5. Latin America
11.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.5.4. Brazil
11.5.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.5.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.5.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.5.5. Rest of LATAM
11.5.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.5.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.5.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
Chapter 12. Company Profiles
12.1. Cisco Systems, Inc.
12.1.1. Company Overview
12.1.2. Product Offerings
12.1.3. Financial Performance
12.1.4. Recent Initiatives
12.2. Palo Alto Networks, Inc.
12.2.1. Company Overview
12.2.2. Product Offerings
12.2.3. Financial Performance
12.2.4. Recent Initiatives
12.3. Microsoft Corporation
12.3.1. Company Overview
12.3.2. Product Offerings
12.3.3. Financial Performance
12.3.4. Recent Initiatives
12.4. Symantec Corporation (now part of Broadcom Inc.)
12.4.1. Company Overview
12.4.2. Product Offerings
12.4.3. Financial Performance
12.4.4. Recent Initiatives
12.5. Okta, Inc.
12.5.1. Company Overview
12.5.2. Product Offerings
12.5.3. Financial Performance
12.5.4. Recent Initiatives
12.6. IBM Corporation
12.6.1. Company Overview
12.6.2. Product Offerings
12.6.3. Financial Performance
12.6.4. Recent Initiatives
12.7. Check Point Software Technologies Ltd.
12.7.1. Company Overview
12.7.2. Product Offerings
12.7.3. Financial Performance
12.7.4. Recent Initiatives
12.8. Akamai Technologies, Inc.
12.8.1. Company Overview
12.8.2. Product Offerings
12.8.3. Financial Performance
12.8.4. Recent Initiatives
12.9. Fortinet, Inc.
12.9.1. Company Overview
12.9.2. Product Offerings
12.9.3. Financial Performance
12.9.4. Recent Initiatives
12.10. CyberArk Software Ltd.
12.10.1. Company Overview
12.10.2. Product Offerings
12.10.3. Financial Performance
12.10.4. Recent Initiatives
Chapter 13. Research Methodology
13.1. Primary Research
13.2. Secondary Research
13.3. Assumptions
Chapter 14. Appendix
14.1. About Us
14.2. Glossary of Terms
About Us:
Our team comprises a dedicated group of research analysts and management consultants who are driven by a unified vision: assisting individuals and organizations in realizing their strategic objectives, both immediate and long-term, through the provision of comprehensive research services. At Precedence Research, we have positioned ourselves to cater to the needs of a diverse range of entities, including established companies, startups, and non-profit organizations across various sectors. Our expertise extends to industries such as packaging, automotive, healthcare, chemicals and materials, industrial automation, consumer products, electronics and semiconductors, IT and telecommunications, and energy. With a wealth of experience within our ranks, our skilled analysts are equipped with extensive knowledge of the research landscape.
Contact Us
Precedence Research
Apt 1408 1785 Riverside Drive Ottawa, ON, K1G 3T7, Canada
Call: +1 9197 992 333
Email: sales@precedenceresearch.com
